Cyber Security: Is Your Organisation Prepared?
Increasing availability of technology and devices along with recent changes in legislation, means the cyber security landscape continues to evolve. This change means responsibility can no longer solely reside with the IT department or provider. Cyber Security requires a holistic approach between functions and employees. Since technology is forever evolving, our knowledge of cyber security must evolve with it. Training and communication should be an ongoing activity throughout the organisation. It must become part of our daily working practises and thinking.
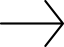
GBE Converge prides itself in providing information, training and security solutions to ensure our clients remain protected, aware and current. Key causes of human cyber security issues in the UK include:
- General carelessness
- IT employee failure to follow policies and procedures
- End user failure to follow policies and procedures
- Lack of expertise with networks, servers and other infrastructure
- Lack of expertise with websites and applications
- Failure to get up to speed with new threats

Information based on extensive research and studies carried out by an industry leading vendor neutral association, CompTIA (www.comptia.org)

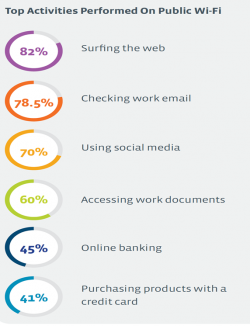
Unprotected WIFI Networks
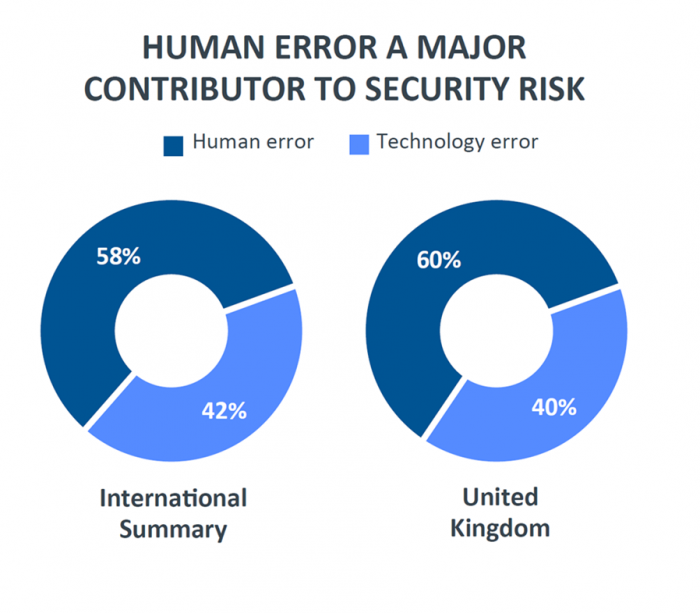
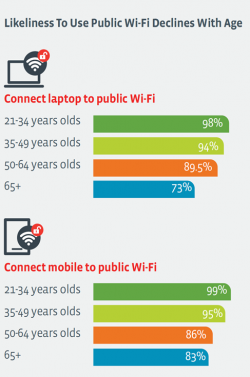
- 94% of employees connect their laptop or mobile devices to public Wi-Fi networks
- 69% of this group handle work-related data while doing so
This means that anyone using these public networks can potentially spy on your organisations confidential data. It is also worth considering that the likelihood of connecting to unsecured wireless networks negatively correlates with age. This is likely due to the increasing expectation of consistent real-time data.
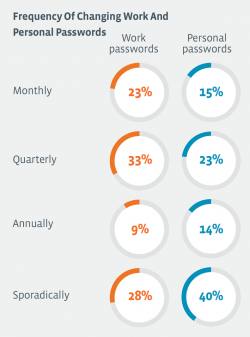
Poor Password Habits
- 49% of workers have at least 10 account logins but only 34% have at least 10 unique username and password combinations
- 36% use their work email address for personal accounts
- 38% use work passwords for personal accounts
Taken together, this means that some workers are re-purposing their work account credentials across multiple personal services. This generates more points of exposure for an organisation and can be difficult to address without better training to spur behavioural changes.
The issue with USB Sticks
Despite the accessibility of free and enterprise-grade file sharing apps and the convenience of email, plenty of employees (58%) rely on USB-based storage drives to transfer files across devices. This presents significant security risks, especially when the data suggest users are willing to use unfamiliar USB storage devices:
- More than 35% have borrowed someone else’s USB stick to copy or transfer a file
- 22% of employees would hypothetically pick up a USB stick they found in public and a staggering 84% of this group would go so far as to plug the USB into one of their own devices
In summary, our IT landscape will continue to develop. The need for constant, accessible, real-time data will only increase. This makes it impossible to completely eliminate cyber attacks. However, it is possible to significantly reduce the risks of one happening within your organisation.
How can GBE Converge help minimise security risks within your business?
IT Audits
GBE Converge has highly skilled engineers who are experienced in auditing complex infrastructure and can produce detailed reports with suggested recommendations for improvement and actions to meet vendors’ and industry’s best practises.
Security Audits
Creating a secure environment is a challenging task for any business. New exploits are designed every day, legislation is evolving regularly, vendors introduce new features and improvements more often than ever before. GBE Converge offers security audits to help you implement the best possible IT security to keep your business secure and protected.
Business Continuity and Disaster Recovery
In the current business climate, IT is an integral part of any organisation and aligning the IT strategy with the business one is not an easy task. Understanding the business requirements and direction is what we do. Our designs are not IT infrastructure designs, they are business continuity designs, and we adapt IT to business strategy so you can ensure your business is stronger and more competitive.
 Previous
Previous